Difference between revisions of "Tutorial:CodeInjection EditableValues"
(Created page with 'Category:Tutorial Category:Auto Assembler Category:Code Injection {{DISPLAYTITLE:Code Injection - Editable values}} This tutorial builds on the subject of code injec…') |
(→Packed Multiplier) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 160: | Line 160: | ||
</pre> | </pre> | ||
| − | Starting with a script like above; let's add a float (single precision floating point), and | + | Starting with a script like above; let's add a float (single precision floating point), and multiply XMM1. |
<pre> | <pre> | ||
define(address, "game.exe"+123ABC) | define(address, "game.exe"+123ABC) | ||
| Line 173: | Line 173: | ||
label(fltHealthMultiplier) // we need a unque name, | label(fltHealthMultiplier) // we need a unque name, | ||
| − | // and I like to indicate the value type in the name (i.e.: " | + | // and I like to indicate the value type in the name (i.e.: "flt" for float). |
registerSymbol(fltHealthMultiplier) | registerSymbol(fltHealthMultiplier) | ||
| Line 241: | Line 241: | ||
</pre> | </pre> | ||
| − | Starting with a script like above; let's add some floats (single precision floating point), and | + | Starting with a script like above; let's add some floats (single precision floating point), and multiply XMM1 with a packed instruction. For an aligned instruction we need to be at an address ending in 0x0, and for a packed instruction we'll need a value that spans 0x10 bytes (0x0 to 0xF). |
<pre> | <pre> | ||
define(address, "game.exe"+123ABC) | define(address, "game.exe"+123ABC) | ||
| Line 254: | Line 254: | ||
label(fltHealthMultiplier) // we need a unque name, | label(fltHealthMultiplier) // we need a unque name, | ||
| − | // and I like to indicate the value type in the name (i.e.: " | + | // and I like to indicate the value type in the name (i.e.: "flt" for float). |
registerSymbol(fltHealthMultiplier) | registerSymbol(fltHealthMultiplier) | ||
Latest revision as of 13:38, 23 April 2018
This tutorial builds on the subject of code injection, and starts from a working script. Pleas start here: Code Injection - full
Any game will work but I will be using Windows Solitaire.
First you will need to find an Integer. If unsure how to find values see: Finding values - Integers
Contents
Finding the injection point[edit]
After you have found the address of the score then we can find the injection point. Where this is depends on what we want to do so in Windows Solitaire the score decreases over timer, lets make it increase the score, But here let's make it a value that can be changed from the Cheat table without editing the script.
If you followed along with the Code Injection - full tutorial you should have a script like this.
define(address,"solitaire.exe"+396CC)
define(bytes,41 83 43 14 FE)
[ENABLE]
assert(address,bytes)
alloc(newmem,$1000,address) // '$' before a nuber is a short hand for '0x' (hex).
label(code)
label(return)
newmem:
code:
add dword ptr [r11+14],02
jmp return
address:
jmp newmem
return:
[DISABLE]
address:
db bytes
// add dword ptr [r11+14],-02
dealloc(newmem)
So let's add a value that we can change the value of on the CT.
Adding an Editable Value[edit]
So we'll need some memory, which we have some allocated so let's just create a label and register the symbol. We need to register the symbol to be able to access it else where. We can also use align to align the memory because we will just put it at the end of the allocated memory.
define(address,"solitaire.exe"+396CC)
define(bytes,41 83 43 14 FE)
[ENABLE]
assert(address,bytes)
alloc(newmem,0x400,address)
label(code)
label(return)
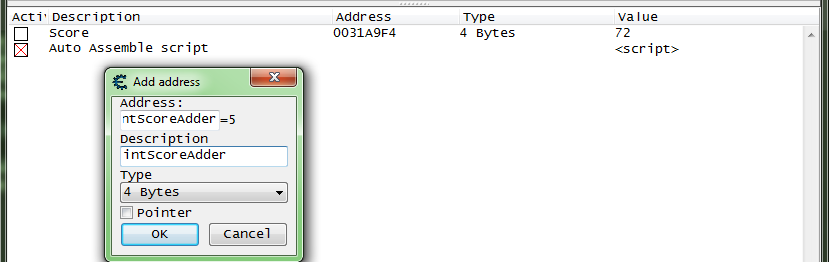
label(intScoreAdder) // we need a unque name,
// and I like to indicate the value type in the name (i.e.: "int" for integer).
registerSymbol(intScoreAdder)
newmem:
code:
push rax // push/save the registory.
mov eax,[intScoreAdder] // EAX is 32 bits of RAX
add [r11+14],eax // the size is determinded by the size of the registory.
pop rax // pop/restore the registory.
jmp return
align 10 CC // align the memory to be assebled.
intScoreAdder:
dd (int)5 // we could just use 'dd 5' as decimal 5 is equal to hex 5
// or the short hand for an integer 'dd #5'.
address:
jmp newmem
return:
[DISABLE]
address:
db bytes
// add dword ptr [r11+14],-02
dealloc(newmem)
So now let's enable the script and add the address to the CT.
Adding the Address a CT[edit]
And that gives us a changeable value that is used inside the script.
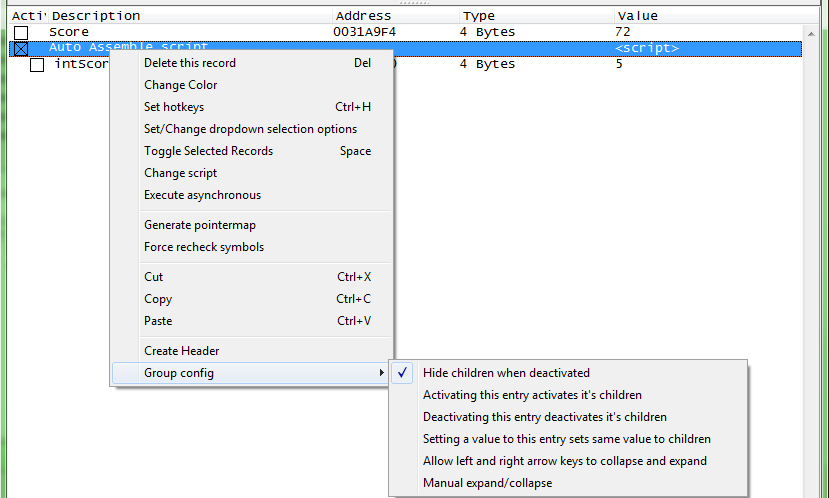
You can set the address as a child of the script, and right click the address record to enable the Hide children when deactivated option under Group config.
Working with Floats[edit]
Health Damage Multiplier[edit]
Let's say you have an injection point that looks like this, and it's effecting health, and XMM1 holds the damage value.
subss xmm0,xmm1 movss [rsi],xmm0
It could even be space apart, all we need is the "subss xmm0,xmm1" in the injection script.
subss xmm0,xmm1 // ... movss [rsi],xmm0
So let's add a damage multiplier.
define(address, "game.exe"+123ABC)
define(bytes, F3 0F 5C C1 F3 0F 11 06)
[ENABLE]
assert(address, bytes)
alloc(newmem, 0x400, address)
label(code)
label(return)
newmem:
code:
subss xmm0,xmm1
movss [rsi],xmm0
jmp return
address:
jmp newmem
nop
nop
nop
return:
[DISABLE]
address:
db bytes
dealloc(newmem)
Starting with a script like above; let's add a float (single precision floating point), and multiply XMM1.
define(address, "game.exe"+123ABC)
define(bytes, F3 0F 5C C1 F3 0F 11 06)
[ENABLE]
assert(address, bytes)
alloc(newmem, 0x400, address)
label(code)
label(return)
label(fltHealthMultiplier) // we need a unque name,
// and I like to indicate the value type in the name (i.e.: "flt" for float).
registerSymbol(fltHealthMultiplier)
newmem:
code:
mulss xmm1,[fltHealthMultiplier]
subss xmm0,xmm1
movss [rsi],xmm0
jmp return
align 10 CC // align the memory to be assebled.
fltHealthMultiplier:
dd (float)0.25
address:
jmp newmem
nop
nop
nop
return:
[DISABLE]
address:
db bytes
dealloc(newmem)
Packed Multiplier[edit]
Let's say you have an injection point that looks like this, and it's effecting health and shield, and XMM1 holds the damage values for both.
subps xmm0,xmm1 movaps [rsi],xmm0
define(address, "game.exe"+123ABC)
define(bytes, 0F 5C C1 0F 29 06)
[ENABLE]
assert(address, bytes)
alloc(newmem, 0x400, address)
label(code)
label(return)
newmem:
code:
subss xmm0,xmm1
movss [rsi],xmm0
jmp return
address:
jmp newmem
nop
return:
[DISABLE]
address:
db bytes
dealloc(newmem)
Starting with a script like above; let's add some floats (single precision floating point), and multiply XMM1 with a packed instruction. For an aligned instruction we need to be at an address ending in 0x0, and for a packed instruction we'll need a value that spans 0x10 bytes (0x0 to 0xF).
define(address, "game.exe"+123ABC)
define(bytes, 0F 5C C1 0F 29 06)
[ENABLE]
assert(address, bytes)
alloc(newmem, 0x400, address)
label(code)
label(return)
label(fltHealthMultiplier) // we need a unque name,
// and I like to indicate the value type in the name (i.e.: "flt" for float).
registerSymbol(fltHealthMultiplier)
newmem:
code:
mulps xmm1,[fltHealthMultiplier]
subps xmm0,xmm1
movaps [rsi],xmm0
jmp return
align 10 CC // align the memory to be assebled. Alignment is required for an aligned instruction.
fltHealthMultiplier:
dd (float)0.25
dd (float)0.35
dd (float)1 // Any values you don't want to change set the multilpier to 1
dd (float)1
address:
jmp newmem
nop
return:
[DISABLE]
address:
db bytes
dealloc(newmem)
To add the values to a CT just set the value type to float and the address for the first one to "fltHealthMultiplier" and the address for the second to "fltHealthMultiplier+4".
See also[edit]
- Code Injection - basic
- Code Injection - full
- Code Injection - editable values
- Code injection
- Tutorials