Difference between revisions of "Auto Assembler Example 2"
Jump to navigation
Jump to search
| Line 13: | Line 13: | ||
# Replace original code in the game with a jmp to my code | # Replace original code in the game with a jmp to my code | ||
| − | Note that since we're replacing | + | Note that since we're replacing these three instructions above with the ''jmp'' instruction, we have to execute them in our code. |
<pre> | <pre> | ||
[ENABLE] | [ENABLE] | ||
alloc(GodCode,512) // allocate memory for our injected code | alloc(GodCode,512) // allocate memory for our injected code | ||
| − | label(GodReturn) // where we will jump back to | + | label(GodReturn) // GodReturn label is where we will jump back to |
registersymbol(GodCode) | registersymbol(GodCode) | ||
Latest revision as of 17:09, 17 July 2020
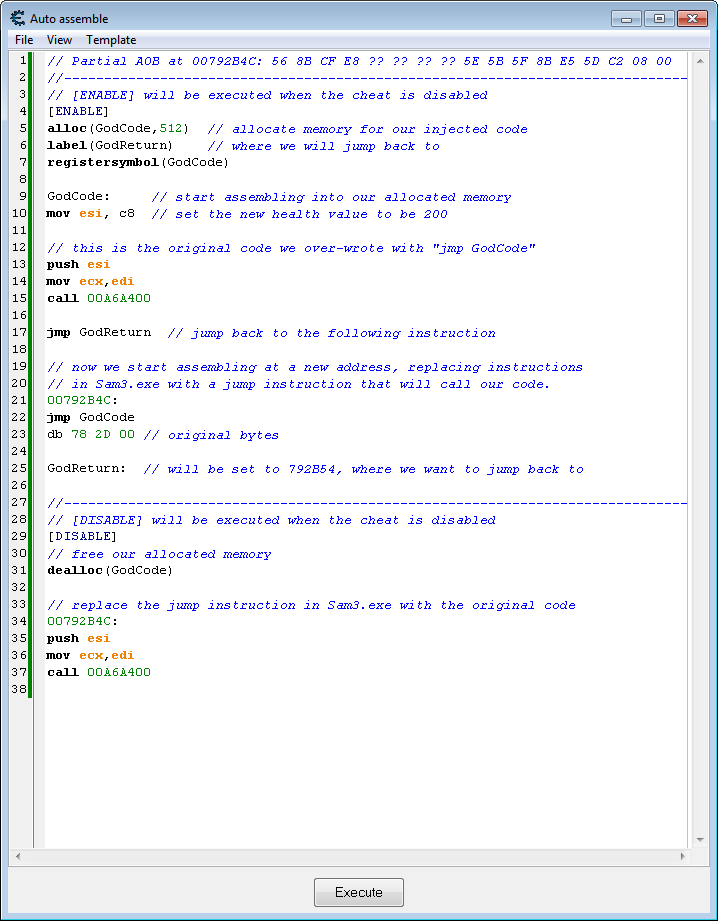
I found the following code that calls a function to set the player's health when he is injured. The player's new health is in the ESI register:
00792B4C - 56 - push esi 00792B4D - 8B CF - mov ecx,edi 00792B4F - E8 AC782D00 - call 00A6A400
To keep the player at full health, I decided just to change the value of ESI to be 200. Here's a script that does several things on ENABLE:
- Allocate memory for my code inside the opened process
- Assemble my code and write it into the allocated memory
- Replace original code in the game with a jmp to my code
Note that since we're replacing these three instructions above with the jmp instruction, we have to execute them in our code.
[ENABLE] alloc(GodCode,512) // allocate memory for our injected code label(GodReturn) // GodReturn label is where we will jump back to registersymbol(GodCode) GodCode: // start assembling into our allocated memory mov esi, c8 // set the new health value to be 200 // this is the original code we over-wrote with "jmp GodCode" push esi mov ecx,edi call 00A6A400 jmp GodReturn // jump back to the following instruction // now we start assembling at a new address, replacing instructions // in Sam3.exe with a jump instruction that will call our code. 00792B4C: jmp GodCode db 78 2D 00 // original bytes GodReturn: // will be set to 792B54, where we want to jump back to
When disabling, we just free the memory we allocated and assemble the original instructions back into place:
[DISABLE] // free our allocated memory dealloc(GodCode) // replace the jump instruction in Sam3.exe with the original code 00792B4C: push esi mov ecx,edi call 00A6A400